What Is Session Hijacking Attack ?
Session hijacking, also known as TCP session hijacking, is a method of taking over a Web user session by surreptitiously obtaining the session ID and masquerading as the authorized user. Once the user's session ID has been accessed (through session prediction), the attacker can masquerade as that user and do anything the user is authorized to do on the network.
The session ID is normally stored within a cookie or URL. For most communications, authentication procedures are carried out at set up. Session hijacking takes advantage of that practice by intruding in real time, during a session. The intrusion may or may not be detectable, depending on the user's level of technical knowledge and the nature of the attack. If a Web site does not respond in the normal or expected way to user input or stops responding altogether for an unknown reason, session hijacking is a possible cause.
Step By Step Explanation Of How To Carry Out This Attack ?
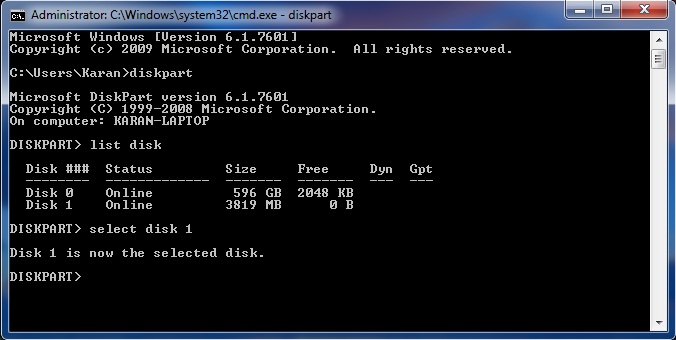
First of all, you would need to connect to an unsecured wireless connection that others are using. Then we start capturing packets transferred over this network. Note that your wireless adapter needs to support monitor mode to scan all packets transferred over a network. you can check your wi-fi card specifications to see if it supports monitor mode.
We would then need to use a network sniffing tool so sniff packets transferred over the network. In this case, I am using a tool called Wireshark (
Download From Here). Within wireshark, there is a menu called "Capture"; Under the capture menu, select interfaces from that menu, and a list of your interfaces will come up
.
Next you select Start Next to the interface that you have enabled monitor mode on. most times it is the interface that is capturing the most packets. In my case, Microsoft interface is capturing the most packets, so i will select to start capturing with the microsoft interface. You would leave wireshark to capture packets for a couple of seconds depending on the amount of persons currently using the network. Say 30 seconds if 10 people currently are using the network, or 30 minutes if there is barely network activity going on. While capturing, wireshark will look something like this.
After capturing a certain amount of packets, or running the capture for a certain amount of time, stop it by clicking on the stop current capture button.
After stopping the capture, you will need to look for the user's facebook session cookie which, hopefully was transferred in one of the packets captured. to find this cookie, use the wireshark search which can be found by pressing "ctrl + f" on your keyboard. In this search interface, select Find: By "String"; Search In: "Packet Details". and Filter by the string "Cookie".
When you press find, if there is a cookie, this search will find it, if no cookie was captured, you will have to start back at step 2. However, if youre lucky and some cookies we're captured, when you search for cookie, your interface will come up looking like this in the diagram below. You would notice the cookie next to the arrow contains lots of data, to get the data. the next thing you do is to right click on the cookie and click copy->description.
After copying the description, paste it in a text file, and separate each variable to a new line (note the end of every variable is depicted by a semicolon eg - c_user=100002316516702;). After some research and experimenting, i figured out that facebook authenticated the user session by 2 cookies called c_user and xs. Therefore you will only need the values of these cookies, and then need to inject them into your browser. Before injecting the cookies, here is what my facebook page looked like:
The next thing you would need to do is to inject this information as your own cookie. so firstly you would need to install a cookie manager extension for your browser, I'm using firefox Cookie Manager. After installing this extension, you will find it under Tools->cookie manager. The interface for cookie manager looks like this:
The first thing we would need to do is to clear all cookies, so clear all the cookies you currently have. Then select the "Add Cookie" link to add a new cookie. The first cookie you will add is the c_user cookie which will have the following information:: Domain - ".facebook.com", name-"c_user", value-"the value you copied earlier from the wireshark scanning" and the Path-"/"; leave the isSecure and Expires On values to default:
The next thing you do is to hit the "Add" button and the cookie is saved. Repeat the same steps to add the xs cookie with all of the same information, except the value, which would be the xs value you have.
After adding these 2 cookies, just go to facebook.com, refresh the page and... Boom!! you will see you are logged in as that user whose cookie information you stole. Here is my facebook page after i injected those cookies:














.png)
.jpg)
.jpg)




